Measuring Occurrence of DNSSEC Validation
Passive and Active Measurements Conference
Hong Kong, March 19, 2013


Universität Duisburg-Essen
Verteilte Systeme
Verteilte Systeme
Matthäus Wander
1











example.net. IN A 1.2.3.4 example.net. IN RRSIG A 5 3 600 20120519... m1TWzfNDMg8NpgTo4i...

example.net. IN DNSKEY 256 3 8 BQEAAAABv5hDo9fIU91cSFaDmnNPg...


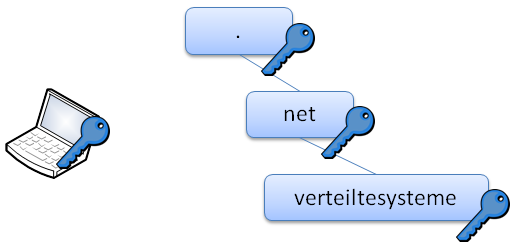
verteiltesysteme.net. IN NS ns1.verteiltesysteme.net. verteiltesysteme.net. IN NS ns2.verteiltesysteme.net. verteiltesysteme.net. IN DS 61908 5 1 3497D121F4C91369E95DC73D8... verteiltesysteme.net. IN DS 61908 5 2 2F87866A60C3603F447658AC3... verteiltesysteme.net. IN RRSIG DS 8 2 86400 20130103051550 2012122... ns1.verteiltesysteme.net. IN A 134.91.78.139 ns2.verteiltesysteme.net. IN A 134.91.78.141
verteiltesysteme.net. IN DNSKEY 257 3 5 BQEAAAABy5oBPRz/mSEcFYXlcL...




verteiltesysteme.net
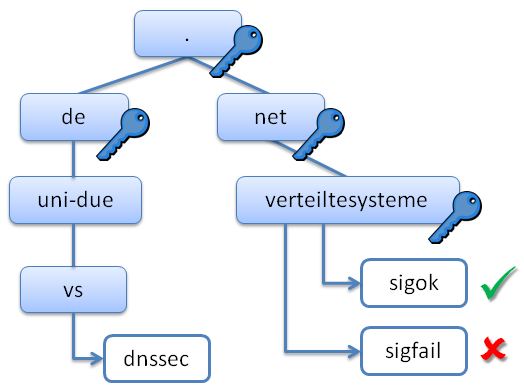
sigok with valid signature
with valid signature
sigfail with broken signature
with broken signature


sigfail domain name
domain name
sigok domain name
domain name


sigok and
and sigfail
<img src="http://dnssec.vs.uni-due.de/r/a" alt="" height="1" width="1"> <img src="http://dnssec.vs.uni-due.de/r/b" alt="" height="1" width="1">
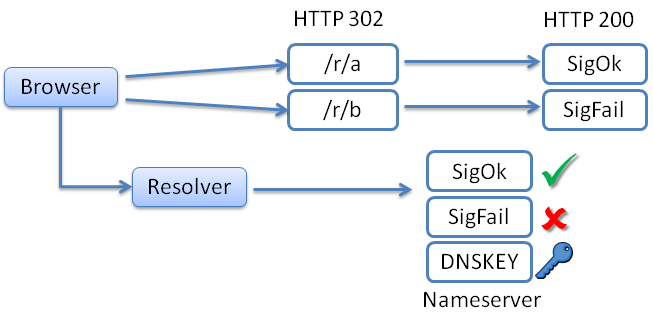


77.181.135.120 "GET /ok.png?aa53 HTTP/1.1" 200 413
62.53.190.69#22782: query: aa53.sigok.verteiltesysteme.net IN A -ED
http://ID.sigok.verteiltesysteme.net/ok.png?ID
ID \(:=\) hex(SHA256(client_ip))[0:4]


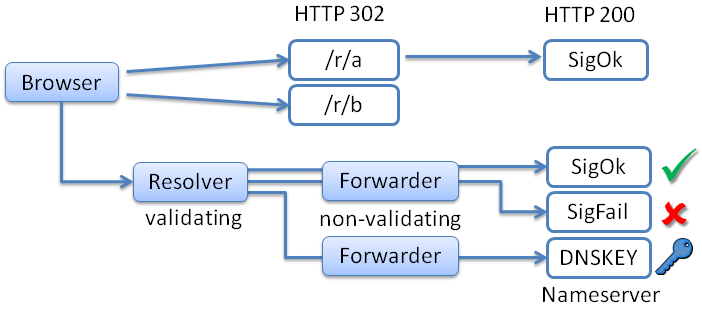
sigfail might fail to load for unrelated reasons → false positive
might fail to load for unrelated reasons → false positive
sigok to exclude some fault sources, e.g.:
to exclude some fault sources, e.g.:
sigfail loads,
loads, sigok fails
fails



sigok and
and sigfail
sigok
sigfail HTTP query OR
HTTP query OR
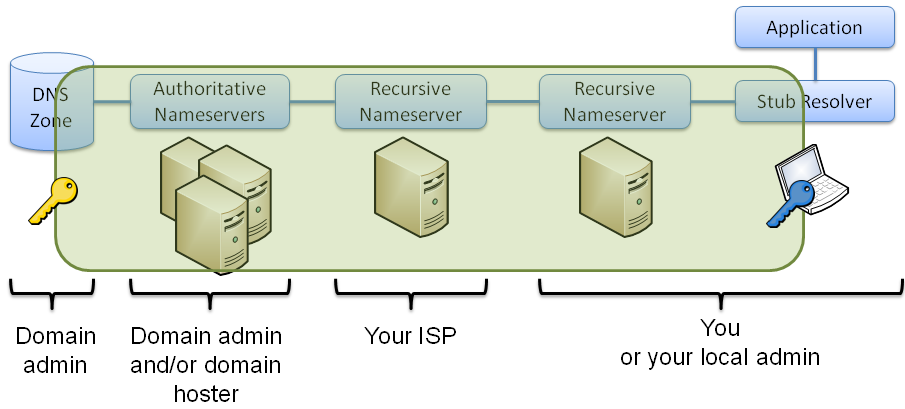
DNSSEC OK flag

| Estimate ratio of false positives:
|


 query is missing
query is missing
 via IP address, not ID
via IP address, not ID


 is missing (0.14%)
is missing (0.14%)






|
|


| No. | AS | Organization | Count | \(\frac{V}{V_{total}}\) | \(\frac{V}{V+N}\) | client=resolver |
|---|---|---|---|---|---|---|
| 1. | 7922 | Comcast | 2786 | 29.2% | 71.3% | 0.9% |
| 2. | 29562 | KabelBW | 1417 | 14.9% | 87.4% | 0.4% |
| 3. | 8767 | M-Net | 519 | 5.4% | 42.8% | 4.6% |
| 4. | 3301 | TeliaSonera | 297 | 3.1% | 76.9% | 1.7% |
| 5. | 5610 | O2 Czech | 279 | 2.9% | 72.3% | 1.4% |
| 6. | 29484 | rub.de | 198 | 2.1% | 46.0% | 0.0% |
| 7. | 2119 | Telenor | 188 | 2.0% | 53.9% | 1.1% |
| 8. | 680 | DFN | 152 | 1.6% | 4.3% | 3.9% |
| 9. | 6661 | pt.lu | 145 | 1.5% | 83.8% | 0.0% |
| 10. | 1257 | Tele2 | 127 | 1.3% | 53.4% | 0.8% |
| 7083 other AS | 3433 | 36.0% | 2.0% | 17.8% | ||