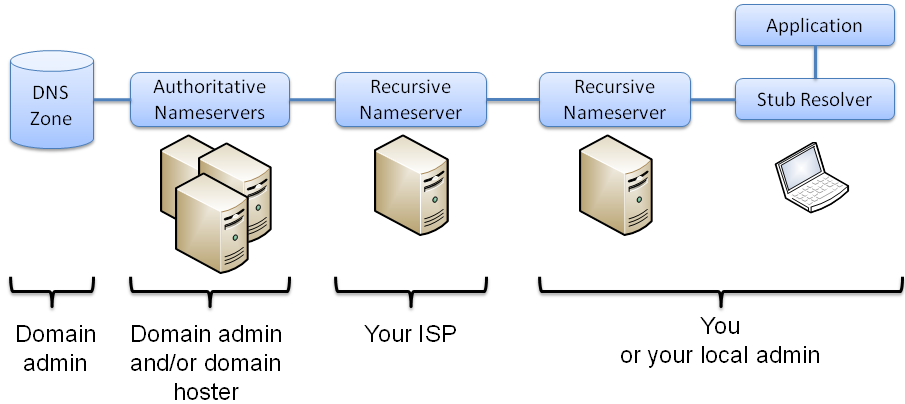
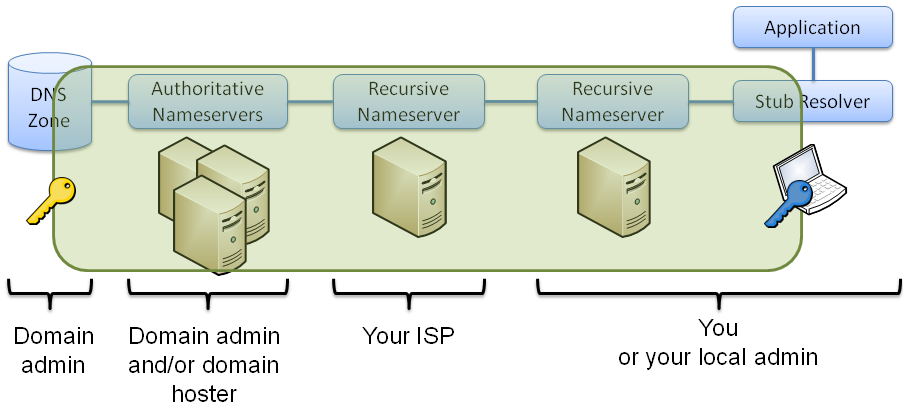
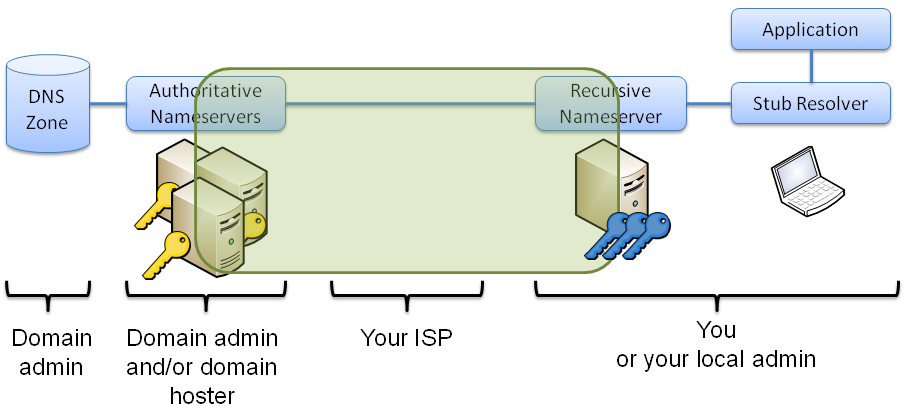
Secure Name Resolution
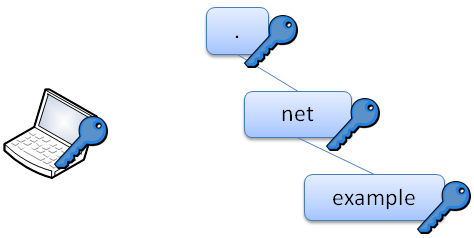
DNSSEC, DNSCurve and Namecoin






example.net. IN A 1.2.3.4 example.net. IN RRSIG A 5 3 600 20120519... m1TWzfNDMg8NpgTo4i...

example.net. IN DNSKEY 256 3 8 BQEAAAABv5hDo9fIU91cSFaDmnNPg...
verteiltesysteme.net. IN NS ns1.verteiltesysteme.net. verteiltesysteme.net. IN NS ns2.verteiltesysteme.net. verteiltesysteme.net. IN DS 61908 5 1 3497D121F4C91369E95DC73D8... verteiltesysteme.net. IN DS 61908 5 2 2F87866A60C3603F447658AC3... verteiltesysteme.net. IN RRSIG DS 8 2 86400 20130103051550 2012122... ns1.verteiltesysteme.net. IN A 134.91.78.139 ns2.verteiltesysteme.net. IN A 134.91.78.141
verteiltesysteme.net. IN DNSKEY 257 3 5 BQEAAAABy5oBPRz/mSEcFYXlcL...
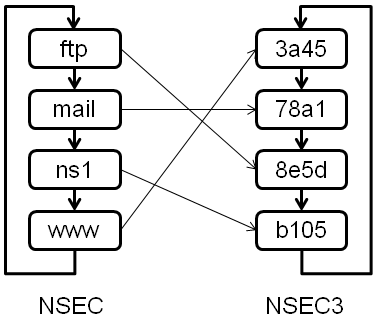
ftp IN NSEC mail
3a45 IN NSEC3 78a1
| TLD | Signed | Total | Percentage | Reference |
|---|---|---|---|---|
| br | 352k | 3M | 11% | [3] |
| com | 139k | 100M | 0.1% | [4] |
| cz | 380k | 1M | 38% | [5] |
| net | 29k | 15M | 0.2% | [4] |
| nl | 1.3M | 5.1M | 26% | [6] [7] |
| se | 148k | 1.3M | 12% | [8] |
| Alternatives:
|
| Date | Domain | Reason | Reference |
|---|---|---|---|
| 2012-12-27 | mil | signatures expired | [dnssec-deployment] |
| 2012-12-07 | arpa | APNIC reverse lookups failed after hardware fault | [dnssec-deployment] |
| 2012-01-18 | nasa.gov | KSK rollover failed | [11] |
| 2011-07-25 | nist.gov | no valid DNSKEY record | [dnssec-deployment] |
| 2011-06-15 | co.th | rollover from NSEC to NSEC3 failed | [dnssec-deployment] |
| 2011-01-03 | gi | signatures expired | [dnssec-deployment] |
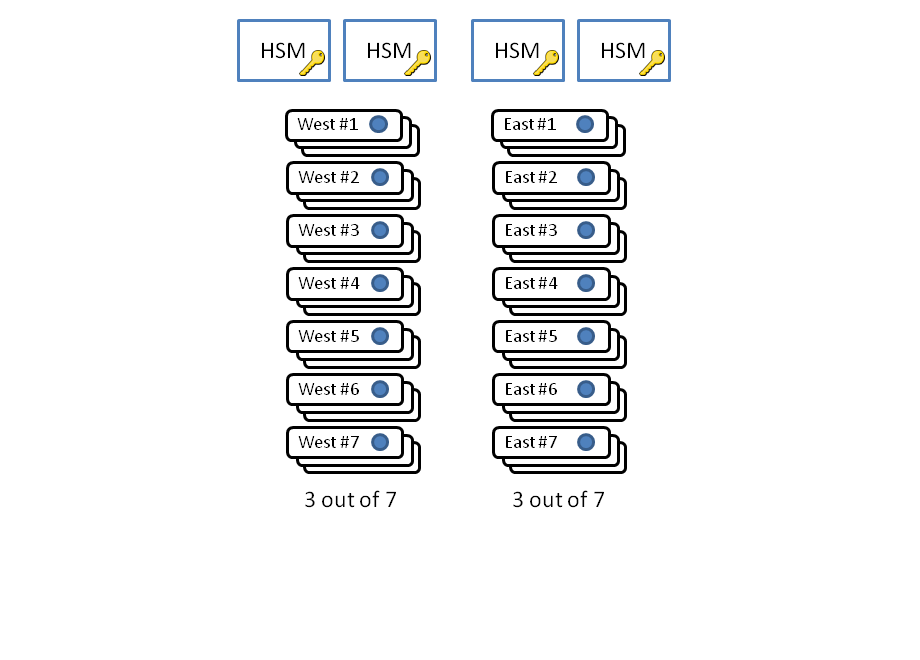
| 2010-10-07 | be | signatures expired | [dnssec-deployment] |
| 2010-09-15 | mozilla.org | DS published before signed zone was online | [dnssec-deployment] |
| 2010-09-11 | uk | inconsistent ZSK after hardware fault | [12] |
| more: http://dns.comcast.net | |||
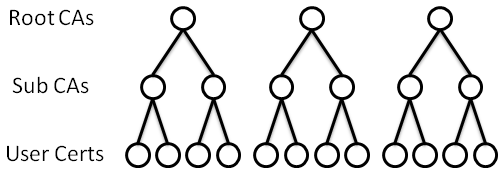 |
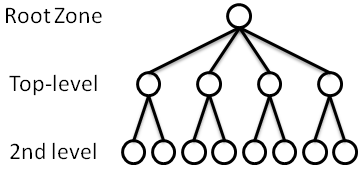
|
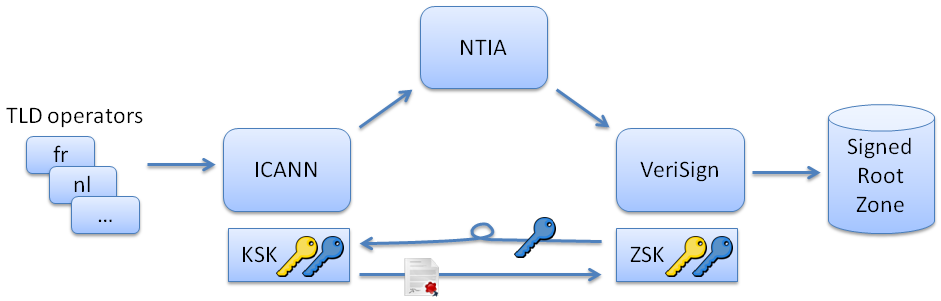
|  |
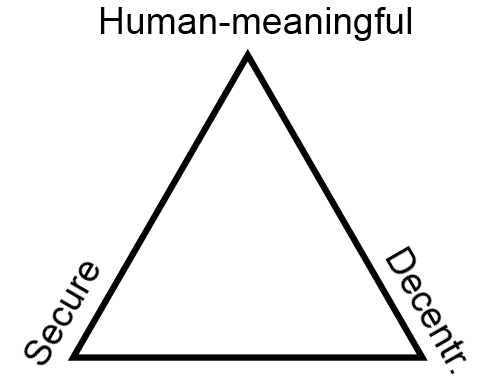
|  |

example.net. IN NS uz5wmnnvkbdd29t79yzg9fr2s2rx[...].example.net.
[1] DNSCurve: The nsec3walker tool, 2011-01-03
[2] ICANN: TLD DNSSEC Report, 2012-12-26
[3] Registro.br: Domínios Registrados por DPN, 2012-12-26
[4] VeriSign: Domains Secured with DNSSEC, 2012-12-26
[5] CZ.NIC: Statistics, 2012-12-25
[6] PowerDNS: Total number of DNSSEC delegations in the .NL zone, 2012-12-01
[7] SIDN: Statistics, 2012-12-01
[8] .SE: Domain Growth per Type, 2012-12-26
[9] RFC 3514: The Security Flag in the IPv4 Header, 2003-04-01
[10] RIPE NCC: Status for k.root-servers.net, 2012-08-09
[11] Comcast DNS: Analysis of NASA.GOV Validation Failure, 2012-01-24
[12] Simon McCalla: DNSSEC incident report, 2010-09-24
[13] Keith Cowing (NASA Watch): Comcast Blocks Customer Access to NASA.gov, 2012-01-18
[14] P. Vixie, V. Schryver: DNS Response Rate Limiting (DNS RRL), 2012-06
[15] Ondřej Caletka: Wildcard domains DNSSEC resolver test
[16] Red Hat Bugzilla: Bug 824219
[17] Anonymous: The Collateral Damage of Internet Censorship by DNS Injection, 2012-07-03
[18] P. Eckersleyer & J. Burns: Is the SSLiverse a Safe Place?, 2010
[19] RFC 6698: The DNS-Based Authentication of Named Entities (DANE) Transport Layer Security (TLS) Protocol: TLSA, 2012-08
[20] RFC 5011: Automated Updates of DNS Security (DNSSEC) Trust Anchors
[21] Image credit: Microsoft Bing Maps
[22] Image credit: Terremark Inc.
[23] Image credit: Kim Davies, KSK Ceremony 1, 2010-06-16
[24] Image credit: ICANN, http://data.iana.org/ksk-ceremony/
[25]
Fingerprint of root KSK as of 2012-12-26:
“. IN DS 19036 8 2 49AAC11D7B6F6446702E54A1607371607A1A41855200FD2CE1CDDE32F24E8FB5”
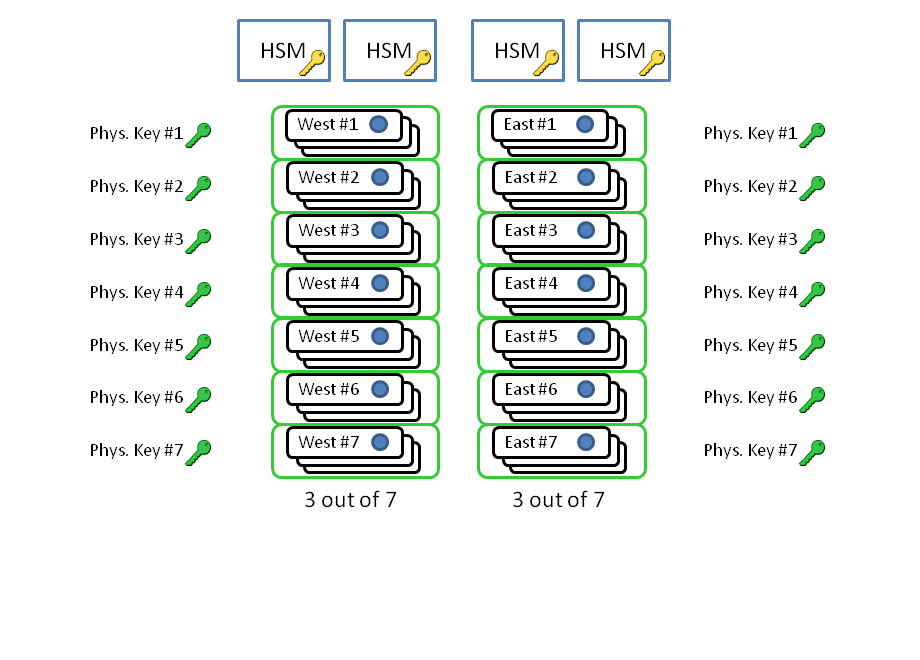
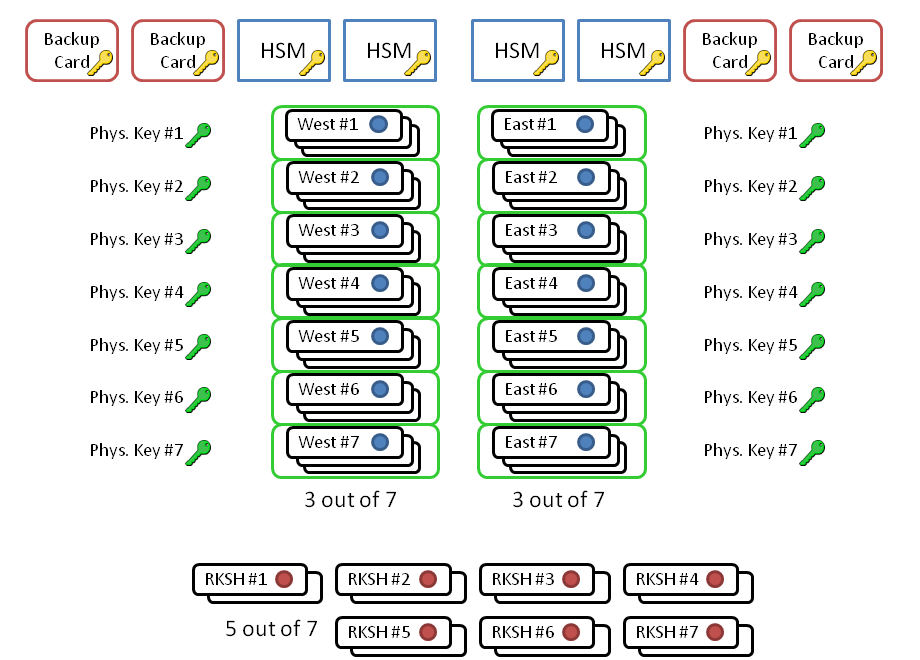
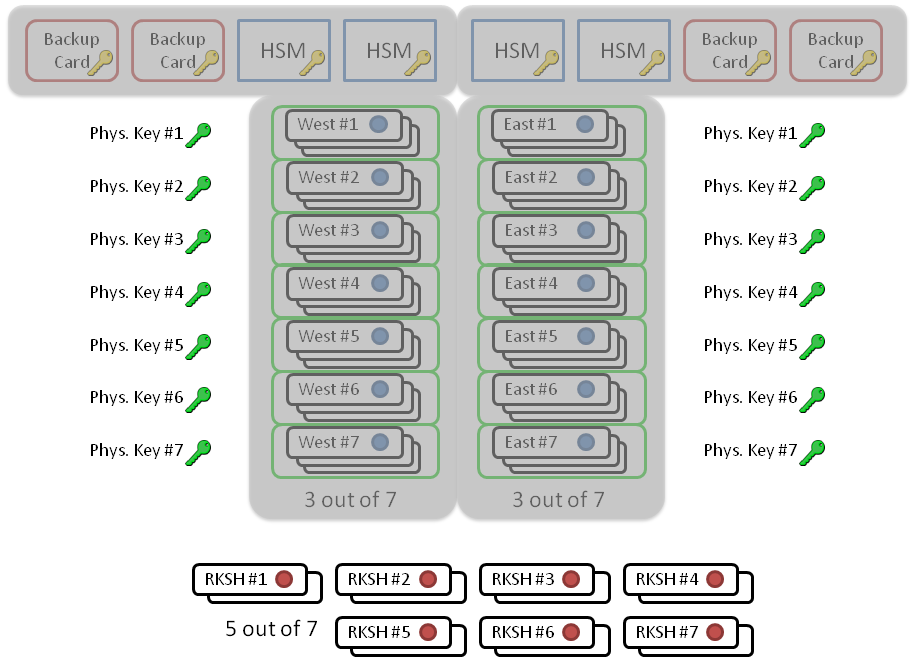
[26] Jakob Schlyter: Hardware Security Modules
[27] T. Okubo et al.: DNSSEC Practice Statement for the Root Zone ZSK operator, 2010-05-28
[28] http://dnscurve.org/
[29] Matthew Dempsky: DNSCurve: Link-Level Security for the Domain Name System, 2010-02-26
[30] Image credit: http://root-servers.org & Google Maps, 2012-12-27
[31] http://dot-bit.org
[32] Matthäus Wander: How Bitcoin Works, 2011-06-29
[33] Zooko Wilcox-O'Hearn: Names: Decentralized, Secure, Human-Meaningful: Choose Two, 2003-09-22
[34] Image credit: Sven Wolter, Wikimedia Commons