Measuring Occurrence of DNSSEC Validation
August 21, 2012


Universität Duisburg-Essen
Verteilte Systeme
Verteilte Systeme
Matthäus Wander
1




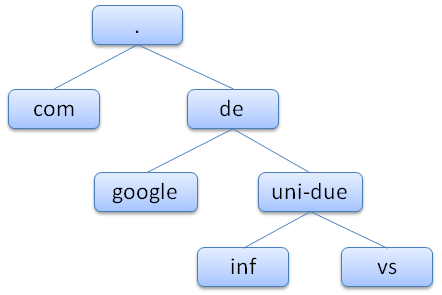
vs.uni-due.de. IN NS dns1.vs.uni-due.de. vs.uni-due.de. IN NS dns2.vs.uni-due.de. dns1.vs.uni-due.de. IN A 134.91.78.133 dns2.vs.uni-due.de. IN A 134.91.78.131


www.evil-attacker.net. IN NS www.your-bank.com. www.your-bank.com. IN A 6.6.6.6




example.net. IN A 1.2.3.4 example.net. IN RRSIG A 5 3 600 20120519... m1TWzfNDMg8NpgTo4i...

example.net. IN DNSKEY 256 3 8 BQEAAAABv5hDo9fIU91cSFaDmnNPg...


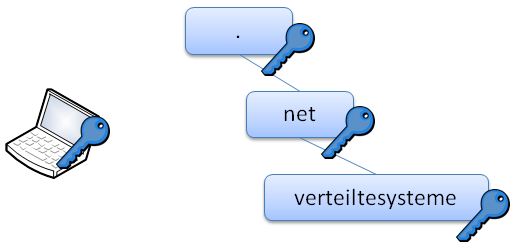
verteiltesysteme.net. IN NS ns1.verteiltesysteme.net. verteiltesysteme.net. IN NS ns2.verteiltesysteme.net. verteiltesysteme.net. IN DS 61908 5 1 3497D121F4C91369E95DC73D8... verteiltesysteme.net. IN RRSIG DS 8 2 86400 20120812041548 2012080... ns1.verteiltesysteme.net. IN A 134.91.78.139 ns2.verteiltesysteme.net. IN A 134.91.78.141




| TLD | Signed | Total | Percentage | Reference |
|---|---|---|---|---|
| br | 305k | 3M | 10% | [2] |
| com | 69k | 100M | <0.1% | [3] |
| cz | 355k | 952k | 37% | [4] |
| net | 15k | 15M | 0.1% | [3] |
| nl | 531k | 5M | 11% | [5] [6] |
| se | 139k | 1.3M | 10% | [7] |


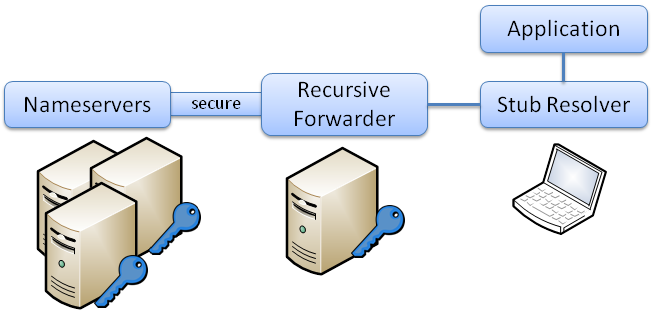 |
Table 2:
Validating Stub Resolvers
|




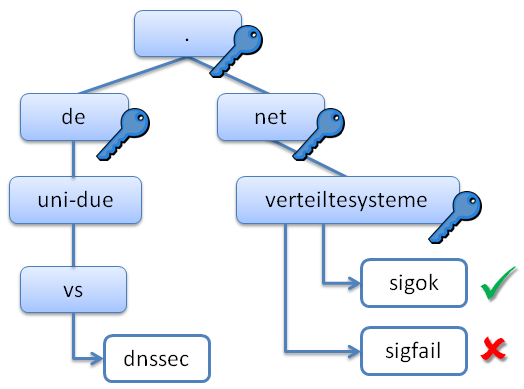
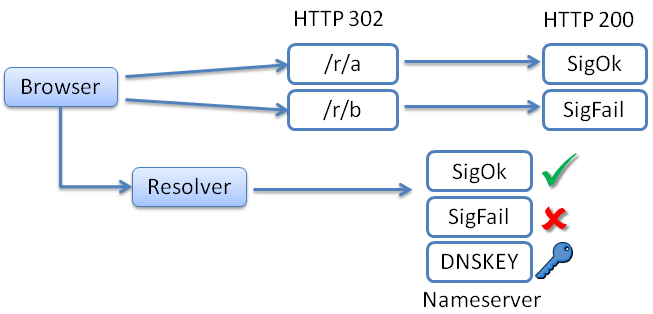
verteiltesysteme.net
sigok with valid signature
with valid signature
sigfail with broken signature
with broken signature


sigfail domain name
domain name
sigok domain name
domain name


sigok and
and sigfail
<img src="http://dnssec.vs.uni-due.de/r/a" alt="" height="1" width="1"> <img src="http://dnssec.vs.uni-due.de/r/b" alt="" height="1" width="1">


77.181.135.120 - - [07/May/2012:23:28:24 +0200] "GET /ok.png?aa53 HTTP/1.1" 200 413 "http://dnssec.vs.uni-due.de/" "Opera/9.80 (Windows NT 6.1; WOW64; U; en) Presto/2.10.229 Version/11.62"
07-May-2012 23:24:40.590 info: client 62.53.190.69#22782: query: aa53.sigok.verteiltesysteme.net IN A -ED (134.91.78.139)
http://ID.sigok.verteiltesysteme.net/ok.png?ID
ID \(:=\) hex(SHA256(client_ip))[0:4]


sigfail might fail to load for unrelated reasons → false positive
might fail to load for unrelated reasons → false positive
sigok to exclude some fault sources, e.g.:
to exclude some fault sources, e.g.:
sigfail loads,
loads, sigok fails
fails


test.dnssec-or-not.net. 60 IN CNAME 537e07e4883acd6e.dnssec-or-not.net.






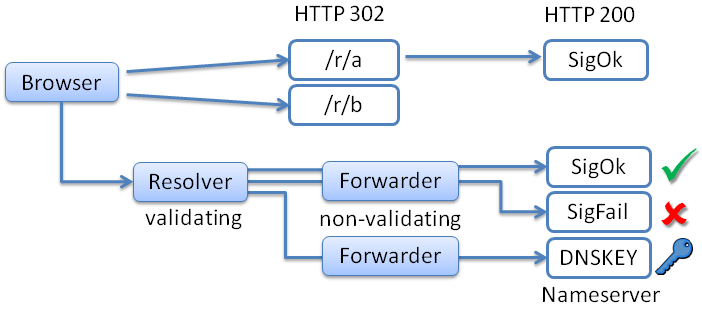
 queried: validation enabled
queried: validation enabled
 not queried: no validation
not queried: no validation

| Test | JS req. | Img req. | Criteria | Mixed validation |
|---|---|---|---|---|
| Uni-DUE interactive | yes | yes | Image loads | negative |
| Uni-DUE hidden | no | yes | Image loads | negative |
| VeriSign | no | no | 3x query retry | potentially positive |
| SIDN | yes | yes | DNSKEY | potentially positive |
| dnssec-failed | no | no | Page loads | negative |


 netsec group
netsec group



sigok and
and sigfail
sigok


| Estimated ratio of false positives:
|




RedirOk[client=188.174.44.11[DE 188.174.*.* AS8767 ppp-188-174-44-11.dynamic.mnet-online.de]] RedirFail[client=188.174.44.11[DE 188.174.*.* AS8767 ppp-188-174-44-11.dynamic.mnet-online.de]] DNS[resolver=208.69.35.17[NL 208.69.32-36.* AS36692 m7.ams.opendns.com],hostname=sigfail,qtype=A] DNS[resolver=208.69.35.17[NL 208.69.32-36.* AS36692 m7.ams.opendns.com],hostname=sigok,qtype=A] SigOk[client=188.174.49.205[DE 188.174.*.* AS8767 ppp-188-174-49-205.dynamic.mnet-online.de]] SigFail[client=188.174.49.205[DE 188.174.*.* AS8767 ppp-188-174-49-205.dynamic.mnet-online.de]]




sigfail query not existing, indicating positive result
query not existing, indicating positive result
 query missing → false positive
query missing → false positive
 via IP address, not ID
via IP address, not ID


| Condition | Count | Filtered |
|---|---|---|
| ID Hash Collision | 11 | yes |
| Inconsistent IP Address | 2581 | no |
| Inconsistent User-Agent | 1820 | yes |
| DNSKEY Missing | 425 | yes |
| 24h IP Blocking | 115093 | yes |











[1] ICANN: TLD DNSSEC Report (2012-08-08)
[2] Registro.br: Domínios Registrados por DPN (2012-08-09)
[3] VeriSign: Domains Secured with DNSSEC (2012-08-08)
[4] CZ.NIC: Statistics (2012-07-31)
[5] PowerDNS: Total number of DNSSEC delegations in the .NL zone (2012-08-09)
[6] SIDN: Statistics (2012-07-31)
[7] .SE: Domain Growth per Type (2012-08-09)
[8] S. Bellovin: The Security Flag in the IPv4 Header, RFC 3514 (2003-04-01)
[9] RIPE NCC: Status for k.root-servers.net (2012-08-09)

